TLS Pool daemon
The TLS protocol is a security cornerstone for online protocols, including for web, sending and receiving email, chat and many more. Unfortunately, its operational aspects do not reflect its importance. TLS Pool is a project that aims at making TLS an easier protocol to operate on.
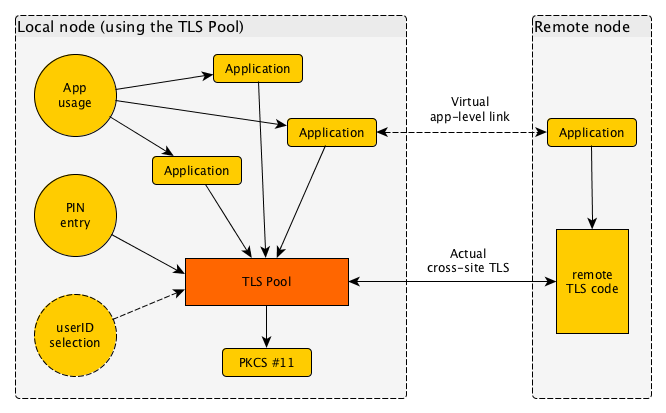
What is the TLS Pool daemon?
The TLS Pool daemon (or "background program") is a program that runs without a visible interface of its own. What it does is translate unprotected traffic into TLS-protected traffic, and vice versa.
When an application has built up a connection and decides to continue over TLS (which may be from the onset or after a so-called STARTTLS handshake with the remote node) it hands over its connection to the TLS Pool daemon and receives a protected link back in return.
Authentication and Authorisation
The TLS Pool daemon handles authentication, which does the following two things:
- provide proof for a local identity, or signal that none will be given;
- validate an identity for the remote node, or otherwise determine that none is given.
Authentication basically answers "who are you?" questions.
Based on a valid identity, the TLS Pool can also arrange for Authorisation. This answers questions like "are you allowed to do this?" based on the validated identity of the authentication phase.
For example, imagine a email list which rejects non-member postings; it could require certificates to be presented upon posting an email, and accept only those that have been signed up for the email list. Authentication would be the establishment of the certificate identity, and authorisation would be the check if the identity is a member of the list.
Interfaces to the daemon
The TLS Pool can be contacted by Applications that wish to use it as a secure transport layer, and for authentication and authorisation. This is done over the Socket Protocol.
The TLS Pool can be contacted by User Interface elements that wish to influence the operation of the TLS Pool in some way. Specifically, to enter PIN codes (or passwords) for access to credentials, and optionally to select one from a number of user identities.
Finally, the TLS Pool contacts a service for proper handling of credentials, over the standardised PKCS #11 interface.
