TLS Pool uses PKCS #11
The TLS protocol is a security cornerstone for online protocols, including for web, sending and receiving email, chat and many more. Unfortunately, its operational aspects do not reflect its importance. TLS Pool is a project that aims at making TLS an easier protocol to operate on.
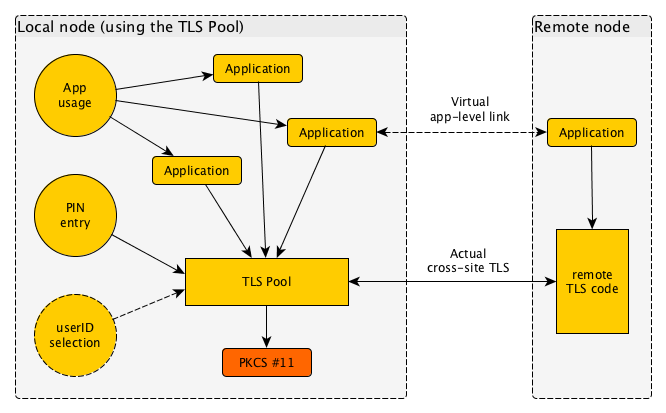
The TLS Pool daemon cannot directly access credentials such as secret keys, but needs to go through the industry-standard interface known as PKCS #11. There is a lively market offering various levels of implementations for this interface, and these can be used under the TLS Pool to secure credentials:
- Software-based modules offer little more than encapsulation of secrets
- USB tokens can store a couple of keys and would never hand them out
- Remote-access libraries can access a remote PKCS #11 implementation
- Hardware Secure Modules are made that plug into a local bus on a computer
- Heavy security industry produces rack-mountable Hardware Security Modules
This diversity leaves the user a choice how secure his setup should be. After removing the token from a system, it is not possible to take actions with secrets that have properly been encapsulated behind PKCS #11.
Note that some of the choices are more suited for a desktop system, while others are more suited to servers.
