TLS Pool desktop usage
The TLS protocol is a security cornerstone for online protocols, including for web, sending and receiving email, chat and many more. Unfortunately, its operational aspects do not reflect its importance. TLS Pool is a project that aims at making TLS an easier protocol to operate on.
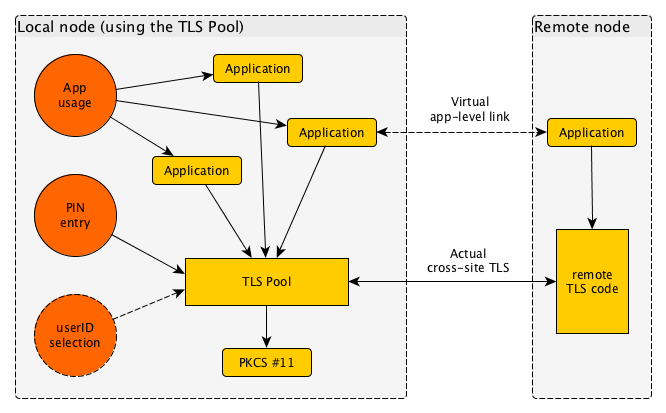
When the TLS Pool is used on a desktop, its use will mean a few modifications; the end user will see a more consistent and more controllable interface with the security layers of the system.
Each their own
Every user on a system runs their own instance of the TLS Pool. This means that credentials of different users are never mixed. Between programs however, this is very well possible.
Token support
The TLS Pool reaches out to secret credentials such as private keys through the industry-standard PKCS #11 interface.
PIN entry
Access over PKCS #11 is protected with a PIN, or a password. This needs to be entered once in a while. With the TLS Pool, this is always done by the same program, and it can be made to light up special parts of the screen to demonstrate its authenticity. This is much more secure than popups that may occur in the browser, mail tool or other; and always looking differently.
UserID selection
An optional instrument that the TLS Pool offers is selection of user identity. A user normally has a user@domain.name format identity, or parhaps just domain.nam. In fact, the same person may use multiple identities. The ability to switch quickly between such identities is a great help with pseudonymous use of network connections.
The selection of the user identity is done with one external program, and this may actually setup rules that select the same identity each time a certain remote TLS endpoint is approached. In addition, a pulldown menu from a menu bar would permit instant change of user identity, or perhaps creating a new one on the spot.
The user identities are uniform, and may map to various security technologies, such as X.509, OpenPGP, OpenSSH, Kerberos5, SRP and so on.
